I try to add Mock MDS device to Reg-client.
I followed:
Now I have user “devicepartner1” with roles: default-roles-mosip, DEVICE_PROVIDER, offline_access, uma_authorization.
Also, I have user “operator01” with roles: Default, GLOBAL_ADMIN, offline_access, REGISTRATION_OPERATOR, REGISTRATION_SUPERVISOR, uma_authorization, ZONAL_ADMIN.
In admin-ui I have added resources: Center, machine and map operator01 to the new center and the new zone.
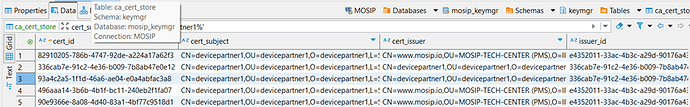
select * from mosip_keymgr.ca_cert_store where cert_subject like ‘%CN=devicepartner1%’
gives me RootCA cert, Intermediate cert and 3 certificates where cert_issuer is MOSIP-TECH-CENTER (PMS):
select * from mosip_master.ca_cert_store where cert_subject like ‘%CN=devicepartner1%’
gives me the same:
When I start MoskMDS I get in logs:
12:12:30.881 [main] DEBUG org.jose4j.jwa.AlgorithmFactoryFactory - Initialized jose4j in 523ms
Because I use self-signed certificates for mosip host, I add next params in command line, when running reg-client:
-Djavax.net.ssl.trustStore=%regpath%mosip-truststore-sha1.jks
-Djavax.net.ssl.trustStorePassword=XXXXX
I try to run reg-client in 2 versions:
Version 1. If I run \reg-client>run.bat
Devices scanning not start, no new messages in MockMDS.
In registration.log:
12:25:16 INFO ClientSetupValidator : Loaded props/mosip-application.properties
12:25:17 INFO SoftwareUpdateUtil : invoking https://regclient.mosip.mosip.local.com/.../MANIFEST.MF
12:25:18 INFO ClientSetupValidator : Checksum validation completed, no patch
12:25:18 INFO ClientIntegrityValidator : Integrity check passed for registration jars
12:25:23 INFO DaoConfig : Setting up datasource, Derby security check OK
12:25:24 INFO TPMClientCryptoServiceImpl : TPM asymmetric key created in 9s
12:25:37 INFO KeyStoreImpl : Loaded OLKeyStoreImpl
12:25:39 INFO RestartController : Sync restart timer started
12:25:40 INFO SoftwareUpdateHandler : Current version 1.2.0.2, no backup found
12:25:40 INFO GlobalParamServiceImpl : Fetched global params
12:25:40 INFO ServiceDelegateUtil : Network check https://api-internal.mosip.mosip.local.com/v1/syncdata/actuator/health
12:25:41 INFO ClientApplication : Login screen initialized and loaded
12:25:47 INFO LoginController : Validating credentials
12:25:50 INFO UserDetailDAOImpl : User not found, userFound=false
12:25:51 INFO AuthTokenUtilService : Fetching Auth Token via PASSWORD
12:25:56 INFO TPMClientCryptoServiceImpl : Completed TPM signing key creation
12:25:56 INFO AuthTokenUtilService : Calling https://api-internal.mosip.mosip.local.com/v1/syncdata/authenticate/useridpwd
12:25:57 INFO LoginServiceImpl : Initial sync start
12:25:57 INFO PolicySyncServiceImpl : getCertificate request {applicationId=KERNEL, referenceId=SIGN}
12:25:57 INFO RestClientAuthAdvice : Adding authZ token to header
12:25:58 ERROR RestClientAuthAdvice : UNKNOWN ERROR >> 500 Internal Server Error on getCertificate
org.springframework.web.client.HttpServerErrorException: 500 Internal Server Error
at io.mosip.registration.util.restclient.RestClientUtil.invokeURL(RestClientUtil.java:68)
Caused by: io.mosip.registration.exception.RegBaseCheckedException: UNKNOWN_ERROR --> 500 Internal Server Error
at io.mosip.registration.util.advice.RestClientAuthAdvice.addAuthZToken(RestClientAuthAdvice.java:86)
...
12:25:58 ERROR PolicySyncServiceImpl : java.lang.reflect.UndeclaredThrowableException
at io.mosip.registration.util.restclient.ServiceDelegateUtil.get(ServiceDelegateUtil.java:148)
Caused by: io.mosip.registration.exception.RegBaseCheckedException: UNKNOWN_ERROR --> 500 Internal Server Error
...
12:25:58 ERROR LoginServiceImpl : REG-SYN-002 --> PublicKey Sync failed
at io.mosip.registration.service.login.impl.LoginServiceImpl.initialSync(LoginServiceImpl.java:320)
Caused by: RegBaseCheckedException: UNKNOWN_ERROR --> 500 Internal Server Error
...
12:25:58 INFO AlertController: Alert generation started and ended
12:26:11 INFO AlertController : Alert closing started and ended
12:26:11 INFO SoftwareUpdateHandler : Version check 1.2.0.2
12:26:11 INFO PageFlow : Preparing page flow map for New Registration, Onboard, UIN Update
12:26:11 INFO SoftwareUpdateHandler : Checking for updates via https://regclient.mosip.mosip.local.com/.../maven-metadata.xml
12:26:11 INFO GlobalParamServiceImpl : SoftwareUpdate flag updated
And with operator01 credentials I can’t login to reg-client.
Version 2. When I start registration-test-utility, in MockMDS logs I see next:
12:49:16.600 [Thread-0] INFO io.mosip.mock.sbi.service.SBIWorker - Request data :: MOSIPDINFO /info HTTP/1.1Host: 127.0.0.1:4501Connection: Keep-AliveUser-Agent: Apache-HttpClient/4.5.7 (Java/11.0.8)Accept-Encoding: gzip,deflate
12:49:16.600 [Thread-0] INFO io.mosip.mock.sbi.service.SBIWorker - Method Name :: MOSIPDINFO
12:49:16.600 [Thread-0] INFO io.mosip.mock.sbi.service.SBIWorker - Method Valid ::
12:49:16.632 [Thread-0] INFO io.mosip.mock.sbi.devicehelper.SBIDeviceHelper - Keystore already cached, nothing to load :: C:\Users\DIL\IdeaProjects\mosip\sourcecode\mosip-mock-services\MockMDS\target
12:49:16.774 [Thread-0] INFO io.mosip.mock.sbi.service.SBIWorker - Response data :: HTTP/1.1 200 OK
Access-Control-Allow-Headers:DNT,X-Mx-ReqToken,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type,X-PINGOTHER,Authorization
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: "OPTIONS, RCAPTURE, CAPTURE, MOSIPDINFO, MOSIPDISC, STREAM, GET, POST"
Access-Control-Allow-Credentials: true
CACHE-CONTROL:no-cache
Content-Length: 27154
Content-Type: application/json
LOCATION: HTTP://127.0.0.1:4501/
Connection: close
[{"deviceInfo":"eyJ4N","error":{"errorCode":"0","errorInfo":"Success"}},{"deviceInfo":"ey","error":{"errorCode":"0","errorInfo":"Success"}},{"deviceInfo":"eyJ","error":{"errorCode":"0","errorInfo":"Success"}}]
12:49:16.790 [Thread-1] INFO io.mosip.mock.sbi.service.SBIWorker - Request data :: MOSIPDINFO /info HTTP/1.1Host: 127.0.0.1:4501Connection: Keep-AliveUser-Agent: Apache-HttpClient/4.5.7 (Java/11.0.8)Accept-Encoding: gzip,deflate
12:49:16.790 [Thread-1] INFO io.mosip.mock.sbi.service.SBIWorker - Method Name :: MOSIPDINFO
12:49:16.790 [Thread-1] INFO io.mosip.mock.sbi.service.SBIWorker - Method Valid ::
12:49:16.800 [Thread-1] INFO io.mosip.mock.sbi.devicehelper.SBIDeviceHelper - Keystore already cached, nothing to load :: C:\Users\DIL\IdeaProjects\mosip\sourcecode\mosip-mock-services\MockMDS\target
12:49:16.853 [Thread-1] INFO io.mosip.mock.sbi.service.SBIWorker - Response data :: HTTP/1.1 200 OK
Access-Control-Allow-Headers:DNT,X-Mx-ReqToken,Keep-Alive,User-Agent,X-Requested-With,If-Modified-Since,Cache-Control,Content-Type,X-PINGOTHER,Authorization
Access-Control-Allow-Origin: *
Access-Control-Allow-Methods: "OPTIONS, RCAPTURE, CAPTURE, MOSIPDINFO, MOSIPDISC, STREAM, GET, POST"
Access-Control-Allow-Credentials: true
CACHE-CONTROL:no-cache
Content-Length: 27154
Content-Type: application/json
LOCATION: HTTP://127.0.0.1:4501/
Connection: close
[{"deviceInfo":"eyJ4N","error":{"errorCode":"0","errorInfo":"Success"}},{"deviceInfo":"ey","error":{"errorCode":"0","errorInfo":"Success"}}]
And in registration.log:
14:07:53,631 INFO DaoConfig : Setting up datasource
14:07:53,647 INFO TPMClientCryptoServiceImpl : Instantiating Platform TPM
14:08:03,935 INFO TPMClientCryptoServiceImpl : Asymmetric Key Creation completed (10s)
14:08:04,820 INFO DaoConfig : Security setup check complete & success
14:08:07,685 INFO KeyStoreImpl : Loaded offline keystore impl
14:08:10,054 INFO BioAPIFactory : Initializing mockvendor SDK (FACE/FINGER/IRIS)
14:08:10,314 INFO RestartController : Restart Timer started
14:08:11,161 INFO SoftwareUpdateHandler : Version 1.2.0.2 verified
14:08:11,406 INFO ServiceDelegateUtil : Health check https://api-internal.mosip.mosip.local.com/v1/syncdata/actuator/health
14:08:11,645 INFO PolicySyncServiceImpl : getCertificate {applicationId=KERNEL, referenceId=SIGN}
14:08:11,681 ERROR RestClientAuthAdvice : 500 Internal Server Error
at io.mosip.registration.util.restclient.RestClientUtil.invokeURL(RestClientUtil.java:68)
Caused by: io.mosip.registration.exception.RegBaseCheckedException: UNKNOWN_ERROR --> 500 Internal Server Error
at io.mosip.registration.util.advice.RestClientAuthAdvice.addAuthZToken(RestClientAuthAdvice.java:86)
14:08:11,685 ERROR LoginServiceImpl : REG-SYN-002 --> PublicKey Sync failed
at io.mosip.registration.service.login.impl.LoginServiceImpl.validateResponse(LoginServiceImpl.java:392)
14:08:11,691 INFO JobConfigurationServiceImpl : Initiating Sync Jobs
14:08:11,763 INFO JobConfigurationServiceImpl : Scheduler initialized, jobs loaded successfully
14:08:11,855 INFO MosipDeviceSpecificationFactory : Checking device info ports 4501–4600
14:08:12,124 INFO MosipDeviceSpecification_SBI_1_0_ProviderImpl : Received device info on port 4501
14:08:12,216 INFO [pool-4-thread-1] i.m.k.p.s.i.PartnerCertificateManagerServiceImpl : pcSessionId - - - Loading CA TrustStore Cache for partnerDomain: DEVICE
14:08:12,235 INFO [pool-4-thread-1] i.m.k.p.s.i.PartnerCertificateManagerServiceImpl : pcSessionId - CertTrustPathValidation - - Certificate Trust Path Validation for domain: DEVICE
14:08:12,236 INFO [pool-4-thread-1] i.m.k.p.s.i.PartnerCertificateManagerServiceImpl : pcSessionId - CertTrustPathValidation - - Total Number of ROOT Trust Found: 1
14:08:12,236 INFO [pool-4-thread-1] i.m.k.p.s.i.PartnerCertificateManagerServiceImpl : pcSessionId - CertTrustPathValidation - - Total Number of INTERMEDIATE Trust Found: 18
14:08:12,242 ERROR MosipDeviceSpecificationHelper : REG-MDM-108 --> Certificate path trust validation failed
14:08:12,242 ERROR MosipDeviceSpecification_SBI_1_0_ProviderImpl : Exception while parsing deviceinfo (NullPointerException)
14:08:12,243 INFO MosipDeviceSpecification_095_ProviderImpl : Parsing device info response (095 dto)
14:08:12,251 ERROR MosipDeviceSpecificationHelper : REG-MDM-108 --> Certificate path trust validation failed (0.9.5)
14:08:12,255 ERROR MosipDeviceSpecificationHelper : REG-MDM-108 --> Certificate path trust validation failed (retry)
14:08:12,259 INFO MosipDeviceSpecification_092_ProviderImpl : Parsing device info response (092 dto)
14:08:12,263 ERROR MosipDeviceSpecification_092_ProviderImpl :
UnrecognizedPropertyException: Unrecognized field "errorCode" (expected "errorcode", "errorinfo")
at io.mosip.registration.mdm.spec_0_9_2.service.impl.MosipDeviceSpecification_092_ProviderImpl.getMdmDevices(...)
And with operator01 credentials I login to reg-client, but don’t have any connected mock devices.