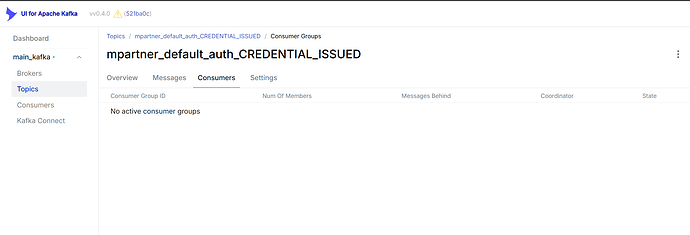
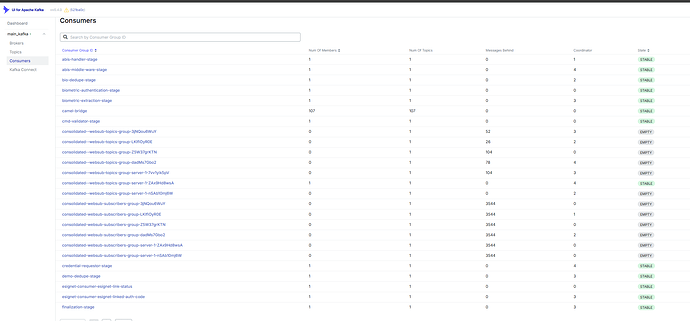
Hi @Varaniya1,
Thank you for the reply.
Here are the logs:
Websub logs:
127.0.0.6 - - [26/Sep/2025:06:56:21 +0000] "GET /hub/actuator/health HTTP/1.1" 200 215 "-" "kube-probe/1.32"
127.0.0.6 - - [26/Sep/2025:06:56:29 +0000] "POST /hub/?hub.mode=publish&hub.topic=mpartner-default-auth/CREDENTIAL_ISSUED HTTP/1.1" 200 17 "-" "Apache-HttpClient/4.5.6 (Java/11.0.16)"
127.0.0.6 - - [26/Sep/2025:06:56:31 +0000] "GET /hub/actuator/health HTTP/1.1" 200 215 "-" "kube-probe/1.32"
IDA internal logs:
{"@timestamp":"2025-09-26T06:56:22.850Z","@version":"1","message":"sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES","logger_name":"io.mosip.kernel.keymanager.hsm.health.HSMHealthCheck","thread_name":"http-nio-8093-exec-7","level":"INFO","level_value":20000,"appName":"id-authentication,id-authentication-internal","traceId":"a1b1e04e4359a76e","spanExportable":"false","req.requestURI":"/idauthentication/v1/internal/actuator/health","X-Span-Export":"false","req.method":"GET","req.userAgent":"kube-probe/1.32","spanId":"a1b1e04e4359a76e","X-B3-SpanId":"a1b1e04e4359a76e","X-B3-TraceId":"a1b1e04e4359a76e","req.remoteHost":"127.0.0.6","req.requestURL":"http://192.168.154.136:8093/idauthentication/v1/internal/actuator/health"}
2025-09-26 06:56:22.850 INFO [id-authentication,id-authentication-internal,a1b1e04e4359a76e,a1b1e04e4359a76e,false] 64 --- [nio-8093-exec-7] i.m.k.k.hsm.health.HSMHealthCheck : sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES
{"@timestamp":"2025-09-26T06:56:22.851Z","level":"ACCESS","level_value":70000,"traceId":"a1b1e04e4359a76e","statusCode":200,"req.requestURI":"/idauthentication/v1/internal/actuator/health","bytesSent":309,"timeTaken":0.049,"appName":"id-authentication,id-authentication-internal","req.userAgent":"kube-probe/1.32","req.xForwardedFor":"-","req.referer":"-","req.method":"GET","req.remoteHost":"127.0.0.6"}
{"@timestamp":"2025-09-26T06:56:32.606Z","@version":"1","message":"sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES","logger_name":"io.mosip.kernel.keymanager.hsm.health.HSMHealthCheck","thread_name":"http-nio-8093-exec-9","level":"INFO","level_value":20000,"appName":"id-authentication,id-authentication-internal","traceId":"ce8958b624c91a13","spanExportable":"false","req.requestURI":"/idauthentication/v1/internal/actuator/health","X-Span-Export":"false","req.method":"GET","req.userAgent":"kube-probe/1.32","spanId":"ce8958b624c91a13","X-B3-SpanId":"ce8958b624c91a13","X-B3-TraceId":"ce8958b624c91a13","req.remoteHost":"127.0.0.6","req.requestURL":"http://192.168.154.136:8093/idauthentication/v1/internal/actuator/health"}
2025-09-26 06:56:32.606 INFO [id-authentication,id-authentication-internal,ce8958b624c91a13,ce8958b624c91a13,false] 64 --- [nio-8093-exec-9] i.m.k.k.hsm.health.HSMHealthCheck : sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES
{"@timestamp":"2025-09-26T06:56:32.607Z","level":"ACCESS","level_value":70000,"traceId":"ce8958b624c91a13","statusCode":200,"req.requestURI":"/idauthentication/v1/internal/actuator/health","bytesSent":309,"timeTaken":0.016,"appName":"id-authentication,id-authentication-internal","req.userAgent":"kube-probe/1.32","req.xForwardedFor":"-","req.referer":"-","req.method":"GET","req.remoteHost":"127.0.0.6"}
{"@timestamp":"2025-09-26T06:56:32.809Z","@version":"1","message":"sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES","logger_name":"io.mosip.kernel.keymanager.hsm.health.HSMHealthCheck","thread_name":"http-nio-8093-exec-10","level":"INFO","level_value":20000,"appName":"id-authentication,id-authentication-internal","traceId":"61e3476eb7fcd531","spanExportable":"false","req.requestURI":"/idauthentication/v1/internal/actuator/health","X-Span-Export":"false","req.method":"GET","req.userAgent":"kube-probe/1.32","spanId":"61e3476eb7fcd531","X-B3-SpanId":"61e3476eb7fcd531","X-B3-TraceId":"61e3476eb7fcd531","req.remoteHost":"127.0.0.6","req.requestURL":"http://192.168.154.136:8093/idauthentication/v1/internal/actuator/health"}
2025-09-26 06:56:32.809 INFO [id-authentication,id-authentication-internal,61e3476eb7fcd531,61e3476eb7fcd531,false] 64 --- [io-8093-exec-10] i.m.k.k.hsm.health.HSMHealthCheck : sessionId - - healthCheck - READ_KEY_SUCCESS, Key Algorithm: AES
{"@timestamp":"2025-09-26T06:56:32.810Z","level":"ACCESS","level_value":70000,"traceId":"61e3476eb7fcd531","statusCode":200,"req.requestURI":"/idauthentication/v1/internal/actuator/health","bytesSent":309,"timeTaken":0.009,"appName":"id-authentication,id-authentication-internal","req.userAgent":"kube-probe/1.32","req.xForwardedFor":"-","req.referer":"-","req.method":"GET","req.remoteHost":"127.0.0.6"}
I can only see health check logs in ida-internal, the event is not being consumed here.
Credential Service logs:
{"@timestamp":"2025-09-26T06:56:29.584Z","@version":"1","message":"service-account-mosip-crereq-client - REQUEST_ID - 18f0144c-8629-48cf-95b1-d837c4856c9c - Building Event JSON Completed.","logger_name":"io.mosip.credentialstore.service.impl.CredentialStoreServiceImpl","thread_name":"http-nio-8095-exec-7","level":"INFO","level_value":20000,"appName":"credential-service,id-repository,application","traceId":"41d495c5fe728d45","spanExportable":"false","req.requestURI":"/v1/credentialservice/issue","X-Span-Export":"false","req.method":"POST","req.userAgent":"Apache-HttpClient/4.5.6 (Java/11.0.16)","spanId":"41d495c5fe728d45","X-B3-SpanId":"41d495c5fe728d45","X-B3-TraceId":"41d495c5fe728d45","req.remoteHost":"127.0.0.6","req.requestURL":"http://credential.idrepo/v1/credentialservice/issue"}
{"@timestamp":"2025-09-26T06:56:29.631Z","@version":"1","message":"published topic mpartner-default-auth/CREDENTIAL_ISSUED update at hub","logger_name":"io.mosip.kernel.websub.api.client.PublisherClientImpl","thread_name":"http-nio-8095-exec-7","level":"INFO","level_value":20000,"appName":"credential-service,id-repository,application","traceId":"41d495c5fe728d45","spanExportable":"false","req.requestURI":"/v1/credentialservice/issue","X-Span-Export":"false","req.method":"POST","req.userAgent":"Apache-HttpClient/4.5.6 (Java/11.0.16)","spanId":"41d495c5fe728d45","X-B3-SpanId":"41d495c5fe728d45","X-B3-TraceId":"41d495c5fe728d45","req.remoteHost":"127.0.0.6","req.requestURL":"http://credential.idrepo/v1/credentialservice/issue"}
{"@timestamp":"2025-09-26T06:56:29.631Z","@version":"1","message":"service-account-mosip-crereq-client - REQUEST_ID - 18f0144c-8629-48cf-95b1-d837c4856c9c - Publish the update successfully","logger_name":"io.mosip.credentialstore.util.WebSubUtil","thread_name":"http-nio-8095-exec-7","level":"INFO","level_value":20000,"appName":"credential-service,id-repository,application","traceId":"41d495c5fe728d45","spanExportable":"false","req.requestURI":"/v1/credentialservice/issue","X-Span-Export":"false","req.method":"POST","req.userAgent":"Apache-HttpClient/4.5.6 (Java/11.0.16)","spanId":"41d495c5fe728d45","X-B3-SpanId":"41d495c5fe728d45","X-B3-TraceId":"41d495c5fe728d45","req.remoteHost":"127.0.0.6","req.requestURL":"http://credential.idrepo/v1/credentialservice/issue"}
{"@timestamp":"2025-09-26T06:56:29.663Z","level":"ACCESS","level_value":70000,"traceId":"41d495c5fe728d45","statusCode":200,"req.requestURI":"/v1/credentialservice/issue","bytesSent":2646,"timeTaken":3.080,"appName":"credential-service,id-repository,application","req.userAgent":"Apache-HttpClient/4.5.6 (Java/11.0.16)","req.xForwardedFor":"-","req.referer":"-","req.method":"POST","req.remoteHost":"127.0.0.6"}
I can see the topic mpartner-default-auth/CREDENTIAL_ISSUED being published from credential service.